NowIntel Cyber Threat Report - 12th December 2023
Ransomeware Royale - LockBit Holds the Crown, BlackCat's 9 Lives Expended? Akira wounds Compass Group Italia and Aqualectra
LockBit Ransomware: The Unstoppable Heavyweight Is Still On Top
ZeroFox's latest intelligence report identifies LockBit as a sustained digital extortion threat globally, encompassing various industries. While LockBit's overall proportion of attacks is diminishing, it still constitutes a significant portion, with 30% in Europe and 25% in North America from January 2022 to September 2023.
Geographical Trends: LockBit's historical underdeployment in North America is changing, with an expected increase from 40% to 50% of victims by the end of 2023. Industries under frequent attack include manufacturing, construction, retail, legal & consulting, and healthcare.
Intrusion Vectors: LockBit employs diverse intrusion methods, such as exploiting internet-facing applications, phishing, external remote services, drive-by compromise, and leveraging valid accounts. Despite the decreasing proportion of attacks, LockBit remains a significant threat.
Evolution and Targets: First identified in September 2019, LockBit operates as a Ransomware-as-a-Service (RaaS), known for its speed and self-propagation capabilities. Recent high-profile attacks include Royal Mail, Boeing, and ICBC. Affiliates are shifting focus towards professional services, education, and finance.
Recommendations: Enhance cybersecurity measures against LockBit's identified intrusion vectors. Regularly update and patch systems, educate employees on phishing threats, and ensure robust backup and recovery mechanisms.
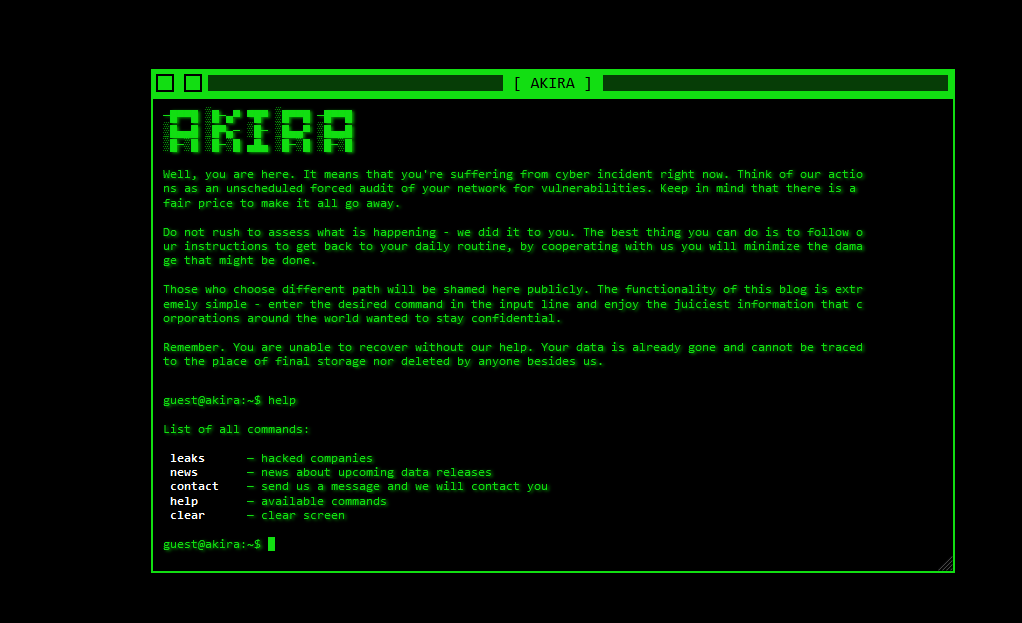
Akira Ransomware Strikes Again: Compass Group Italia and Aqualectra Utility Hit by Data Breach
The infamous Akira ransomware group claims two more victims – Compass Group Italia and Aqualectra Utility. On December 6, 2023, both organizations suffered a breach, compromising sensitive data, including financial records, HR files, and personal information.
Modus Operandi: Akira ransomware employs double extortion tactics, operating as a Ransomware-as-a-Service (RaaS). Primarily targeting companies in the US and Canada, its Tor leak site boasts a distinctive retro appearance.
Wider Impact: Over 80,000 households and businesses relying on Aqualectra's services, the breach jeopardizes data security and privacy.
Recommendations: Initiate incident response procedures, isolate affected systems, and collaborate with Incident responders. Regularly update systems, conduct employee awareness training, and implement robust backup mechanisms.
ALPHV Ransomware Outage: Potential Law Enforcement Action
The ALPHV ransomware gang faces a prolonged outage, sparking rumors of potential law enforcement action. Unique Tor negotiation URLs are down, suggesting a disruption to the ransomware gang's infrastructure.
Possible Law Enforcement Action: Speculations, supported by RedSense Intel, hint at the FBI's involvement in shutting down ALPHV's infrastructure.
Rebrand and Background: Believed to be a rebrand of the DarkSide gang, ALPHV has faced disruptions in the past due to law enforcement actions.
Our two cents: We had a look and could still access the Alphv site on 11/12/23, although it didnt seem down there was an obvious change in content and appearance with both the ‘blog’ and ‘‘collections’’ pages being blank and the search function returning no results. We will continue to monitor the situation.
NHS Trust Admits Historic Data Breaches: Patient Confidentiality at Risk
Cambridge University Hospitals NHS Foundation Trust CEO, Roland Sinker, disclosed two historic data breaches stemming from inadvertent patient data disclosures in response to Freedom of Information (FOI) requests. The first incident, occurring in 2021 but only recently revealed, involved the accidental sharing of personal data related to 22,073 maternity care patients at The Rosie Hospital. This data, accessible via a 'pivot table,' included patient names, hospital numbers, and birth outcomes.
Similarity to PSNI Breach: This data leakage closely mirrors the breach at the Police Service of Northern Ireland (PSNI) earlier this year, where sensitive information was unintentionally shared through an FOI request, hidden by a pivot table.
ICO's Call for Excel Caution: In September, the Information Commissioner’s Office (ICO) urged an immediate end to using Excel spreadsheets for FOI data, issuing guidance on pivot tables. While useful for summarizing large datasets, pivot tables may inadvertently create hidden automatic summaries.
Alert and Further Investigations: The breach came to light when admins at What Do They Know identified and promptly removed the leaked information. Subsequently, the NHS trust conducted a thorough investigation into FOI requests over the past decade, revealing an additional incident in 2021. A spreadsheet sent to Wilmington PLC mistakenly contained names, hospital numbers, and medical information on 373 cancer patients undergoing clinical trials.
Response and Patient Communication: To address the sensitivity of the maternity information, the trust has chosen not to write directly to affected patients. However, the cancer patients involved have received direct communication from the NHS trust, recognizing the potential challenges of self-identification.
Stay vigilant, stay informed, and expect more comprehensive coverage in the weeks to come. For real-time updates and in-depth insights, follow NowIntel!
Best regards,
Your Editor-in-Chief, Ryan Jordan.
Sources: LockBit Ransomware Trends | Akira Ransomware Data Breach | ALPHV Ransomware Outage and Potential Law Enforcement Action | Cambridge Hospitals Excel-Based Data Breaches